Why Data Destruction is a Vital Element of Comprehensive Cyber Security
Why Data Destruction is a Vital Element of Comprehensive Cyber Security
Blog Article
The Importance of Effective Data Damage Practices in Safeguarding Sensitive Information and Ensuring Computer System Safety
In a period where information violations are increasingly common, the significance of effective data destruction methods can not be overemphasized. Organizations face substantial threats when sensitive info is inadequately taken care of, potentially bring about unapproved accessibility and severe monetary repercussions. Carrying out robust information destruction methods not only mitigates these dangers however additionally lines up with legal conformity needs, making sure that organizations support their track record and foster client count on. The question remains: what particular strategies can be used to enhance these techniques, and just how can organizations successfully integrate them into their overall cybersecurity framework?
Comprehending Information Damage
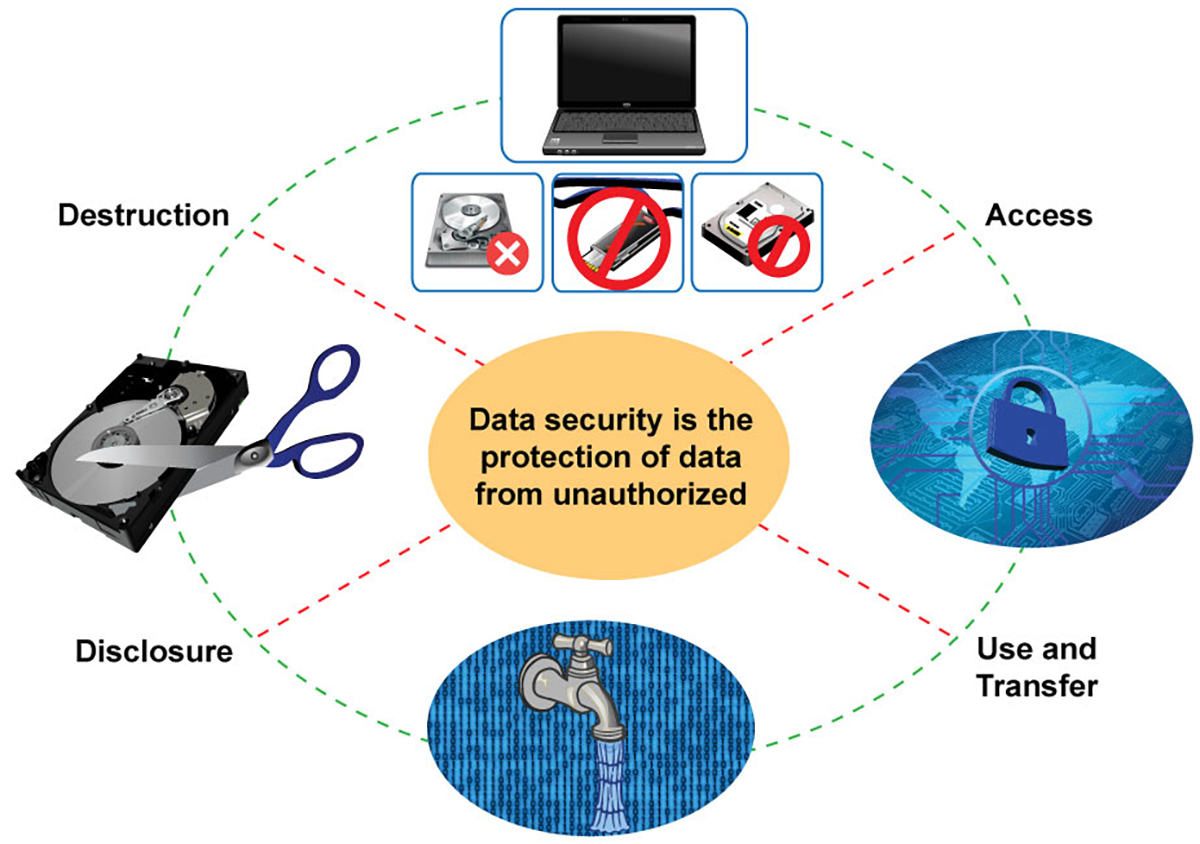
Recognizing information devastation is vital in today's electronic landscape, where delicate information can easily be jeopardized. Efficient data destruction entails not simply making certain but deleting documents that information is irretrievable through extensive methods. This process is essential for organizations that deal with confidential customer information, copyright, or internal papers, as any kind of breach can bring about extreme financial and reputational effects.
Data damage incorporates various strategies, consisting of shredding physical media, degaussing magnetic storage gadgets, and employing software-based services that overwrite information several times. Each method serves a details objective and has to align with the sensitivity of the details being taken care of. As an example, physical devastation is commonly liked for hard disk drives consisting of very private information, while software program methods may be enough for much less sensitive info.
Furthermore, adhering to market criteria and laws, such as the General Information Protection Law (GDPR) or the Medical Insurance Mobility and Accountability Act (HIPAA), is crucial for conformity and to minimize lawful dangers. Organizations needs to develop a robust data devastation plan, train employees on finest techniques, and routinely audit their procedures to make sure that all sensitive information is taken care of securely and properly.
Risks of Inadequate Practices
Insufficient information devastation techniques reveal companies to substantial threats that can have significant repercussions. When sensitive info is not correctly gotten rid of, it remains at risk to unapproved gain access to, which can cause information violations and identification theft. Such incidents not just compromise the safety and security of individuals but likewise stain the organization's reputation, leading to a loss of client trust and possible financial consequences.
In addition, regulatory conformity is increasingly strict in lots of sectors. Failing to follow information devastation laws can lead to large penalties and lawsuits versus organizations. These fines can draw away and stress financial resources interest from core service procedures.
On top of that, the misuse of recurring data can lead to copyright theft or corporate reconnaissance, threatening competitive advantages (data destruction). The influence of insufficient information damage prolongs beyond immediate economic losses; it can likewise result in long-term damages to brand name honesty and market placement

Organizations have to acknowledge that data protection is not only about preventing breaches; it also encompasses the responsible management of data throughout its lifecycle. Neglecting reliable data destruction protocols can have devastating ramifications, emphasizing the requirement for durable measures to reduce these threats.
Best Practices for Information Devastation
Implementing effective information devastation methods is essential for guarding delicate details and keeping conformity with governing standards. Organizations ought to take on a multi-faceted approach to guarantee that information is irretrievable, thus stopping unapproved access and prospective breaches.
First, data should be classified based on level of sensitivity, allowing organizations to use ideal devastation techniques customized to the degree of threat. For electronic information, utilizing software-based data-wiping devices that adhere to sector standards can successfully overwrite existing information. Physical damage methods, such as shredding or degaussing, are crucial for devices that save delicate info, guaranteeing total elimination.
Establishing a clear information retention policy is essential, describing for how long different sorts of info need to be maintained before destruction. Regular audits of information storage space systems are additionally required to recognize unneeded or obsolete information requiring removal.
Furthermore, training staff members on the value of data damage and the certain protocols to follow fosters a society of security within the organization. Lastly, keeping documents of data devastation refines supplies accountability and supports conformity with external guidelines and interior plans. By sticking to these ideal practices, organizations can considerably minimize the dangers connected with data exposure.
Legal and Conformity Considerations
Failing to follow these guidelines can result in serious charges, consisting of considerable penalties and reputational damage. Organizations should execute a durable data destruction policy that lines up with these lawful structures and supplies clear standards on the correct approaches of data disposal, whether physical shredding or electronic wiping.
In addition, preserving paperwork of data damage tasks is important for demonstrating compliance link throughout audits or evaluations. By prioritizing lawful and compliance considerations, companies can improve their information security stance and foster trust fund with clients and stakeholders, eventually adding to a much more safe and secure information management atmosphere.
Advantages of Effective Information Damage
Effective data destruction techniques extend beyond mere conformity; they provide significant benefits to companies that prioritize them. By making sure that sensitive details is irretrievably ruined, companies reduce the threat of data violations and the possible monetary repercussions associated with them. This proactive approach not only safeguards versus unapproved gain access to yet also improves the general trustworthiness of the company in the eyes of stakeholders and clients.
Implementing durable data devastation techniques, such as physical devastation of storage devices or advanced data cleaning techniques, adds to the fortifying of a company's cybersecurity position. data destruction. It lowers the possibility of intellectual residential or find more info commercial property theft and protects proprietary details, therefore keeping an one-upmanship in the marketplace

Verdict
In final thought, efficient data damage techniques are essential for securing sensitive information and boosting general computer system security. Inevitably, a dedication to robust information damage methods promotes a society of obligation, thereby enhancing an organization's cybersecurity position and keeping client count on.

Report this page